Many company IT Security policies insist that workers use only encryptions keys that are generated by the company PKI. That allows the company to recover the encryption keys if they are lost or if the employee leaves the company. PKI issued certificates (which contain the keys) are usualy used with S/MIME in programs like Outlook or Thunderbird.
However, some people wish to use the PGP encryption standard, often because it is required by a customer or other correspondent. This post explains how to export a certificate issued by an enterprise PKI for use in the popular open source encryption program GnuPG. GnuPG follows the PGP standard and can be used to exchange encrypted e-mail with users of the commercial PGP.
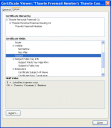
 In this example the certificate is available in the Firexox certificate store. Click to enlarge the image.
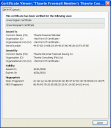
This certificate is for John at Eriugena.org
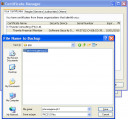
Next backup the certificate onto disk. Firefox uses the extension “.p12” for a certificate that includes the private key.
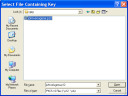
GnuPG cannot import an X.509 certificate. First we have to import the certificate using PGP which can convert it into a PGP type of key.

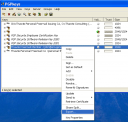
In PGPkeys use the “import” function on the “keys” menu.
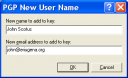
After importing the key, click on it and select “add” and then “name”. Add a user ID to the key. This is required for GnuPG to recognise the user ID and in this case is useful to identify the key.
PGP protects the key using the IDEA algorithm which is not available by default in GnuPG because it is pattented. To get around this you must remove the key protection by changing the passphrase to an empty one. Be careful to delete the key from PGP afterwards or else change back to a non-empty passphrase.
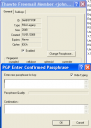
Now export the key. PGP will write the exported key in standard PGP form which can easily be imported into GnuPG.
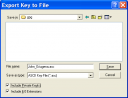
Select “Include Private Key”
Import the key into the GnuPG key ring
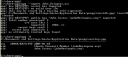
It is very important that you right away edit the key to protect it by adding a passphrase. You can also edit the trust level of the key at this time.
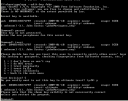
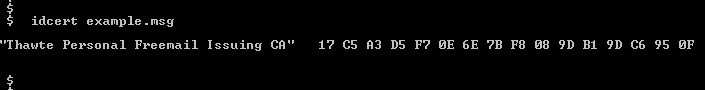
Now test the key by encrypting and then decrypting a message.
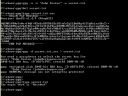
You now have a key in your GnuPG key ring that complies to your company IT Security policy. It came from the company PKI and is therefore archived and recoverable according to the policy.